Hallo zusammen,
wir haben NSP zwischen einer Sophos XG (MTA) und einem Exchange Server eingerichtet.
Leider werden einige eingehende legitime E-Mails abgelehnt.
Wenn ich die Nachrichtenverfolgung exportiere und ich es richtig interpretiere, wird die E-Mail als SPAM/Virus erkannt und abgelehnt, richtig? Dann müsste ich diese als False-Positiv melden damit diese beim nächsten Mal zugestellt wird?
Der Absender bekommt standardmäßig eine NDR?
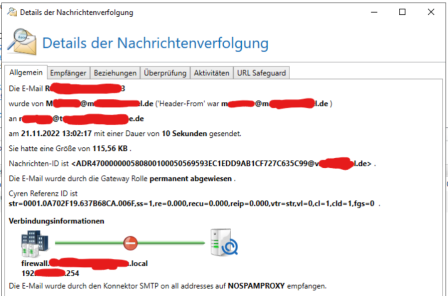
{
"sender": {
"localPart": "Mxxxxxxx",
"domain": "mxxxxxxxxxl.de"
},
"headerFrom": {
"localPart": "mxxxxxxx",
"domain": "mxxxxxxxxxxxl.de"
},
"mailId": "55d83859-9dbf-40e9-8d74-3adabcfbd048",
"messageId": "<ADR470000000580800100050569593EC1EDD9AB1CF727C635C99@vxxxxxxxxl.de>",
"size": 118334,
"subject": "Rxxxxxxxxxxxxxxx3",
"signed": "None",
"encrypted": "None",
"sent": "2022-11-21T13:02:17.807+01:00",
"processingTime": "00:00:10.1900000",
"status": "PermanentlyBlocked",
"ruleName": "All other inbound mails",
"scl": 4,
"validationStatus": "RejectPermanent",
"rejectReason": "SpamOrVirus",
"cyrenReferenceId": "str=0001.0A702F19.637B68CA.006F,ss=1,re=0.000,recu=0.000,reip=0.000,vtr=str,vl=0,cl=1,cld=1,fgs=0",
"processingGatewayRole": "NOSPAMPROXY",
"receiveConnectorName": "SMTP on all addresses",
"clientIPAddress": "192.xxx.xxx.254",
"wasReceivedFromRelayServer": true,
"detailsWereDeleted": false,
"urlSafeguardInfoWasDeleted": false,
"deliveryAttempts": [
{
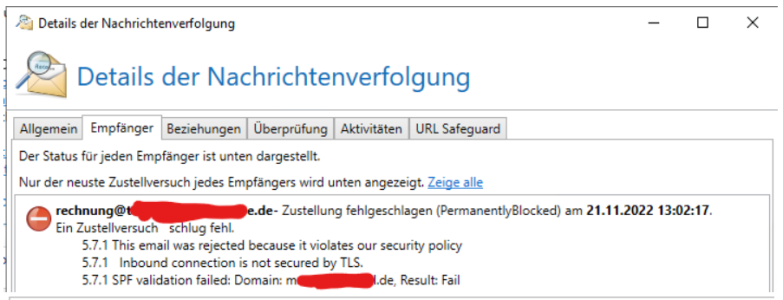
"recipient": "rxxxxxxxx@txxxxxxxxxxxxxxe.de",
"deliveryDate": "2022-11-21T13:02:17.807+01:00",
"status": "PermanentlyBlocked",
"dane": "None",
"statusMessage": "5.7.1 This email was rejected because it violates our security policy\r\n5.7.1 Inbound connection is not secured by TLS.\r\n5.7.1 SPF validation failed: Domain: mxxxxxxxxxxl.de, Result: Fail",
"sendConnector": ""
}
],
"levelOfTrust": {
"domainBonus": 0,
"addressPairingBonus": 0,
"messageIdBonus": 0,
"subjectBonus": 0,
"dsnPoints": 0,
"mailIsTrusted": false,
"scl": 0,
"senderDomainIsFreeMailer": false,
"isSenderAuthenticated": false,
"addressPairingIsWildcardEntry": false,
"wasHeaderFromAddressUsedForValidation": false
},
"actions": [
{
"name": "Malware-Scanner",
"time": "00:00:01.6200000",
"decision": "Pass"
},
{
"name": "CSA-Whitelist",
"time": "00:00:00",
"decision": "Pass"
},
{
"name": "URL Safeguard",
"time": "00:00:00",
"decision": "Pass"
}
],
"attachments": [
{
"name": "Rechnung 9020449343.pdf",
"size": 79746,
"mimeType": "application/pdf",
"sha256Hash": "BAE8850F3BAAFAEC1877C2007BFB9E8A95786DEE3691C8EEAC649FF2935E4B3C"
}
],
"filters": [
{
"name": "Reputationsfilter",
"time": "00:00:08.3000000",
"scl": 4,
"message": "Inbound connection is not secured by TLS.\r\nSPF validation failed: Domain: mxxxxxxxxxl.de, Result: Fail"
},
{
"name": "Cyren AntiSpam",
"time": "00:00:00",
"scl": 0
},
{
"name": "Realtime Blocklists",
"time": "00:00:00",
"scl": 0
},
{
"name": "Spam URI Realtime Blocklists",
"time": "00:00:00.3300000",
"scl": 0
}
],
"operations": [
{
"created": "2022-11-21T13:02:29.593+01:00",
"operation": {
"type": "ConnectionValidation",
"data": "{\"$type\":\"ConnectionValidationEntry\",\"isConnectionSecured\":false,\"childValidationEntries\":[],\"typeName\":\"ConnectionValidation\"}"
}
},
{
"created": "2022-11-21T13:02:29.593+01:00",
"operation": {
"type": "MalwareScan",
"data": "{\"$type\":\"MalwareScanValidationEntry\",\"cyrenZeroHourClassification\":{\"spamClassification\":\"Unknown\",\"virusClassification\":\"Unknown\",\"threatCount\":0,\"detectedThreatType\":\"None\",\"detectedThreatAccuracy\":\"None\",\"threatName\":\"\"},\"action\":\"Pass\",\"infectedMailParts\":[],\"availableScanners\":\"Cyren, CyrenZeroHour\",\"hasAdministrativeNotificationBeenSent\":false,\"childValidationEntries\":[],\"typeName\":\"MalwareScan\"}"
}
},
{
"created": "2022-11-21T13:02:29.593+01:00",
"operation": {
"type": "MailFromHeaderFromAlignmentValidation",
"data": "{\"$type\":\"MailFromHeaderFromAlignmentValidationEntry\",\"areMailFromHeaderFromAligned\":true,\"mailFromAddress\":\"mxxxxxxxxxxxl.de\",\"headerFromAddress\":\"mxxxxxxxxxl.de\",\"childValidationEntries\":[],\"typeName\":\"MailFromHeaderFromAlignmentValidation\"}"
}
},
{
"created": "2022-11-21T13:02:29.593+01:00",
"operation": {
"type": "SenderRecipientValidationEntry",
"data": "{\"$type\":\"SenderRecipientValidationEntry\",\"localAddresses\":[],\"ownedDomainsInHeaderFromDisplayName\":[],\"dnsValidationResultWithAddress\":{\"result\":\"Success\"},\"headerFromContainsAngleBracketsWithInvalidEmailAddress\":false,\"headerFromIsInvalidWithEmptyMailFrom\":false,\"headerFromContainsMultipleAddresses\":false,\"headerFromDisplayNameContainsDomainDifferentFromEmailAddress\":false,\"headerToContainsAtSignOutsideOfEmailAddress\":false,\"headerToContainsAngleBracketsWithInvalidEmailAddress\":false,\"headerToIsEmpty\":false,\"headerFromOrToContainMultipleUnicodeLanguagePlanes\":false,\"headerToDoesNotContainLocalUser\":false,\"childValidationEntries\":[],\"typeName\":\"SenderRecipientValidationEntry\"}"
}
},
{
"created": "2022-11-21T13:02:29.593+01:00",
"operation": {
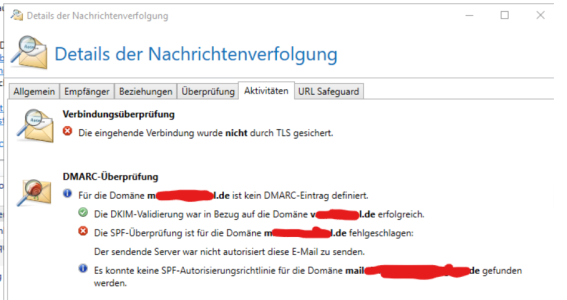
"type": "DmarcValidationEntry",
"data": "{\"$type\":\"DmarcValidationEntry\",\"effectivePolicy\":\"None\",\"rfc5322FromDomain\":\"mxxxxxxxxl.de\",\"validationResult\":\"NoDmarcRecordFound\",\"organizationalDomain\":\"mxxxxxxxxel.de\",\"dkimResult\":[{\"failures\":\"None\",\"authenticatedDomain\":\"vxxxxxxxxl.de\"}],\"spfResult\":[{\"result\":\"Fail\",\"domain\":\"mxxxxxxxxxxxxl.de\"},{\"result\":\"None\",\"domain\":\"mail.xxxxxxxxxxxxxxxxxx.de\"}],\"spfValidationStatus\":\"Validated\",\"dkimAlignment\":false,\"spfAlignment\":false,\"childValidationEntries\":[],\"typeName\":\"DmarcValidationEntry\"}"
}
}
]
}
wir haben NSP zwischen einer Sophos XG (MTA) und einem Exchange Server eingerichtet.
Leider werden einige eingehende legitime E-Mails abgelehnt.
Wenn ich die Nachrichtenverfolgung exportiere und ich es richtig interpretiere, wird die E-Mail als SPAM/Virus erkannt und abgelehnt, richtig? Dann müsste ich diese als False-Positiv melden damit diese beim nächsten Mal zugestellt wird?
Der Absender bekommt standardmäßig eine NDR?
{
"sender": {
"localPart": "Mxxxxxxx",
"domain": "mxxxxxxxxxl.de"
},
"headerFrom": {
"localPart": "mxxxxxxx",
"domain": "mxxxxxxxxxxxl.de"
},
"mailId": "55d83859-9dbf-40e9-8d74-3adabcfbd048",
"messageId": "<ADR470000000580800100050569593EC1EDD9AB1CF727C635C99@vxxxxxxxxl.de>",
"size": 118334,
"subject": "Rxxxxxxxxxxxxxxx3",
"signed": "None",
"encrypted": "None",
"sent": "2022-11-21T13:02:17.807+01:00",
"processingTime": "00:00:10.1900000",
"status": "PermanentlyBlocked",
"ruleName": "All other inbound mails",
"scl": 4,
"validationStatus": "RejectPermanent",
"rejectReason": "SpamOrVirus",
"cyrenReferenceId": "str=0001.0A702F19.637B68CA.006F,ss=1,re=0.000,recu=0.000,reip=0.000,vtr=str,vl=0,cl=1,cld=1,fgs=0",
"processingGatewayRole": "NOSPAMPROXY",
"receiveConnectorName": "SMTP on all addresses",
"clientIPAddress": "192.xxx.xxx.254",
"wasReceivedFromRelayServer": true,
"detailsWereDeleted": false,
"urlSafeguardInfoWasDeleted": false,
"deliveryAttempts": [
{
"recipient": "rxxxxxxxx@txxxxxxxxxxxxxxe.de",
"deliveryDate": "2022-11-21T13:02:17.807+01:00",
"status": "PermanentlyBlocked",
"dane": "None",
"statusMessage": "5.7.1 This email was rejected because it violates our security policy\r\n5.7.1 Inbound connection is not secured by TLS.\r\n5.7.1 SPF validation failed: Domain: mxxxxxxxxxxl.de, Result: Fail",
"sendConnector": ""
}
],
"levelOfTrust": {
"domainBonus": 0,
"addressPairingBonus": 0,
"messageIdBonus": 0,
"subjectBonus": 0,
"dsnPoints": 0,
"mailIsTrusted": false,
"scl": 0,
"senderDomainIsFreeMailer": false,
"isSenderAuthenticated": false,
"addressPairingIsWildcardEntry": false,
"wasHeaderFromAddressUsedForValidation": false
},
"actions": [
{
"name": "Malware-Scanner",
"time": "00:00:01.6200000",
"decision": "Pass"
},
{
"name": "CSA-Whitelist",
"time": "00:00:00",
"decision": "Pass"
},
{
"name": "URL Safeguard",
"time": "00:00:00",
"decision": "Pass"
}
],
"attachments": [
{
"name": "Rechnung 9020449343.pdf",
"size": 79746,
"mimeType": "application/pdf",
"sha256Hash": "BAE8850F3BAAFAEC1877C2007BFB9E8A95786DEE3691C8EEAC649FF2935E4B3C"
}
],
"filters": [
{
"name": "Reputationsfilter",
"time": "00:00:08.3000000",
"scl": 4,
"message": "Inbound connection is not secured by TLS.\r\nSPF validation failed: Domain: mxxxxxxxxxl.de, Result: Fail"
},
{
"name": "Cyren AntiSpam",
"time": "00:00:00",
"scl": 0
},
{
"name": "Realtime Blocklists",
"time": "00:00:00",
"scl": 0
},
{
"name": "Spam URI Realtime Blocklists",
"time": "00:00:00.3300000",
"scl": 0
}
],
"operations": [
{
"created": "2022-11-21T13:02:29.593+01:00",
"operation": {
"type": "ConnectionValidation",
"data": "{\"$type\":\"ConnectionValidationEntry\",\"isConnectionSecured\":false,\"childValidationEntries\":[],\"typeName\":\"ConnectionValidation\"}"
}
},
{
"created": "2022-11-21T13:02:29.593+01:00",
"operation": {
"type": "MalwareScan",
"data": "{\"$type\":\"MalwareScanValidationEntry\",\"cyrenZeroHourClassification\":{\"spamClassification\":\"Unknown\",\"virusClassification\":\"Unknown\",\"threatCount\":0,\"detectedThreatType\":\"None\",\"detectedThreatAccuracy\":\"None\",\"threatName\":\"\"},\"action\":\"Pass\",\"infectedMailParts\":[],\"availableScanners\":\"Cyren, CyrenZeroHour\",\"hasAdministrativeNotificationBeenSent\":false,\"childValidationEntries\":[],\"typeName\":\"MalwareScan\"}"
}
},
{
"created": "2022-11-21T13:02:29.593+01:00",
"operation": {
"type": "MailFromHeaderFromAlignmentValidation",
"data": "{\"$type\":\"MailFromHeaderFromAlignmentValidationEntry\",\"areMailFromHeaderFromAligned\":true,\"mailFromAddress\":\"mxxxxxxxxxxxl.de\",\"headerFromAddress\":\"mxxxxxxxxxl.de\",\"childValidationEntries\":[],\"typeName\":\"MailFromHeaderFromAlignmentValidation\"}"
}
},
{
"created": "2022-11-21T13:02:29.593+01:00",
"operation": {
"type": "SenderRecipientValidationEntry",
"data": "{\"$type\":\"SenderRecipientValidationEntry\",\"localAddresses\":[],\"ownedDomainsInHeaderFromDisplayName\":[],\"dnsValidationResultWithAddress\":{\"result\":\"Success\"},\"headerFromContainsAngleBracketsWithInvalidEmailAddress\":false,\"headerFromIsInvalidWithEmptyMailFrom\":false,\"headerFromContainsMultipleAddresses\":false,\"headerFromDisplayNameContainsDomainDifferentFromEmailAddress\":false,\"headerToContainsAtSignOutsideOfEmailAddress\":false,\"headerToContainsAngleBracketsWithInvalidEmailAddress\":false,\"headerToIsEmpty\":false,\"headerFromOrToContainMultipleUnicodeLanguagePlanes\":false,\"headerToDoesNotContainLocalUser\":false,\"childValidationEntries\":[],\"typeName\":\"SenderRecipientValidationEntry\"}"
}
},
{
"created": "2022-11-21T13:02:29.593+01:00",
"operation": {
"type": "DmarcValidationEntry",
"data": "{\"$type\":\"DmarcValidationEntry\",\"effectivePolicy\":\"None\",\"rfc5322FromDomain\":\"mxxxxxxxxl.de\",\"validationResult\":\"NoDmarcRecordFound\",\"organizationalDomain\":\"mxxxxxxxxel.de\",\"dkimResult\":[{\"failures\":\"None\",\"authenticatedDomain\":\"vxxxxxxxxl.de\"}],\"spfResult\":[{\"result\":\"Fail\",\"domain\":\"mxxxxxxxxxxxxl.de\"},{\"result\":\"None\",\"domain\":\"mail.xxxxxxxxxxxxxxxxxx.de\"}],\"spfValidationStatus\":\"Validated\",\"dkimAlignment\":false,\"spfAlignment\":false,\"childValidationEntries\":[],\"typeName\":\"DmarcValidationEntry\"}"
}
}
]
}